Access Control System – The Virtual & Reliable Security Guard

Every company has two faces and two different types of workforces, one which is the front face of the company and deals with the outside world. They deal with stakeholders like the clients, vendors, sponsors etc. and the other one is the backend which mostly processes the order, services to be provided to the client. You would welcome and invite more people to deal with your frontend or front face workforce, however at the same time you would like to restrict the entry to limited people, to your backend process to keep the confidentiality, maintain the decorum and safety of your equipment and sometimes safety of the people.
For example, if we think about a restaurant, the frontend of a restaurant is a seating and dining area. The waiter and manager are your front faces for the restaurant, you would like to invite and wish that more people should come to your restaurant and have dinner seating at the dining area. However, at the same time, you would like to restrict the entry of them in your kitchen to maintain the cleanliness and decorum of the kitchen. Also, at the same time, you would not encourage them to enter your storeroom, electric server room or CCTVs server rooms for various reasons. Would you deploy a watchman or a security guard at every such access points? NO! first of all, it is not viable economically, second, it will look rude, being in the hospitality industry, to manhandle your clients or other stakeholders.
The solution in such scenarios is to lock the door electronically and keep an Access Control System at the entrance of each such access points. You, as a manager, can decide the access to these areas, even you can restrict the entry of staffs who are not supposed to enter these high-security areas.
Why Access Control System is the best option – operation and working of the Access Control System
Access Control Security System is an electronically configured box, wired internally with door to manage the locking and unlocking of the Gate, Door and Access Points. There are various techniques and protocols on which this box would operate. The system can be running on fingerprint or through RFID based door access control.
In Simple words, the Access Control System lets you, as an owner or as management, decide who will enter where and how. Also, you can link this with your HR ERP and use it as an attendance tool to register the in and out time of each employee. This system also generates reports on the frequency of movement, means how many times an individual goes out and comes back to the office at what interval and for what amount of duration they stay away from the office. The employees also behave in a disciplined manner if they know that their movement is being registered.
The equipment used in Access Control System is very less and has a simple methodology. Step by step methodology in layman words could be explained as below:
- Once the Access Control System Installation is done, the Admin team enters and allot the unique identity to each user and records the information in terms of either RFID, Fingerprint or a password.
- The one of the most important equipment, of all access control devices, is the sensor, the user will give his identity to the sensor whether in terms of RFID Access Control, Fingerprint Access Control or a password for Access Control in Operating System.
- Sensor conveys the information to the inbuilt memory and processor.
- The Access Control Operating System, then searches and matches data in its memory and identifies the user based on the information recorded by the machine.
- If the information matches with the relevant data, the system unlocks the door which is locked through an electromagnetic locking system and allows the user to enter.
- Once the user has entered, the door again gets automatically locked immediately to restrict any other unauthorized entry.
- Same time system sends a message to cloud base register system through the Access Control Panels which connect the system to the internet, to register the entry/exit of the person associated with the given information.
- Management can generate reports through licensed software, or a report can also be pulled through a USB drive, but for a certain period only.
Choose the best Access Control System – Benefits of different types of Access Control Systems
1. Discretionary Access Control (DAC)
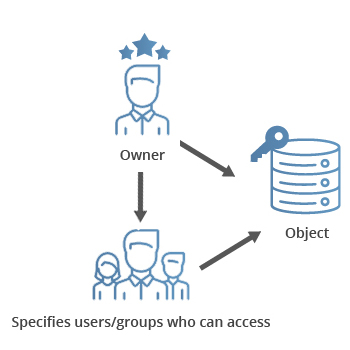 Discretionary Access Control also referred as DAC; this type of access control system gives full authority and decision power to the business owner to decide which people are allowed in a specific location, the permission to enter might be physical or digital.
Discretionary Access Control also referred as DAC; this type of access control system gives full authority and decision power to the business owner to decide which people are allowed in a specific location, the permission to enter might be physical or digital.
DAC gives full freedom and complete ownership of the system to the management to control and interfere at any level whether physically or even in the programme associated with the system, at the same time this vulnerability makes this system least restrictive due to manual control of the system.
You can see this feature as advantageous as well as a drawback or limitation to provide security, as the end-user has the responsibility of security access. If the unauthorized person tracks the password, he can manipulate the system. Also, frequent interference with system’s process may lead to malware or failure of the system.
2. Mandatory Access Control (MAC)
 MAC or Mandatory Access Control system is most preferred and recommended Access Control System for the important organizations, which are more dependent on them. It is preprogrammed and has a fixed process, which cannot be manipulated, changed or controlled by the end-user. It is believed to be the most trusted security tool. It is mainly used in the organizations where confidentiality and access permission are highly important like access to server rooms of CCTV control unit, record rooms and military setups. MAC will classify all end-users and provide them with labels which permit them to gain access through security with established security guidelines.
MAC or Mandatory Access Control system is most preferred and recommended Access Control System for the important organizations, which are more dependent on them. It is preprogrammed and has a fixed process, which cannot be manipulated, changed or controlled by the end-user. It is believed to be the most trusted security tool. It is mainly used in the organizations where confidentiality and access permission are highly important like access to server rooms of CCTV control unit, record rooms and military setups. MAC will classify all end-users and provide them with labels which permit them to gain access through security with established security guidelines.
3. Role-Based Access Control (RBAC)
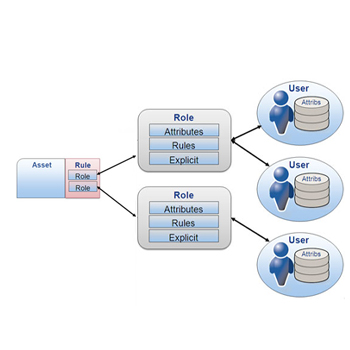 Role-Based Access Control Also known as Rule-Based Access Control, RBAC is the most used and recommended system for the businesses where the use of access control is used as attendance system or for the access based on roles and responsibility of the individual.
Role-Based Access Control Also known as Rule-Based Access Control, RBAC is the most used and recommended system for the businesses where the use of access control is used as attendance system or for the access based on roles and responsibility of the individual.
The rules can be set for each individual like a certain person gets entry only to a certain department. Suppose you have a web a designer, an accountant and an admin person, you can give access to web designer only to designing space, and accountant to accounts department only and an admin might have access to all the department as he as to facilitate all the departments.
RBAC sets the rule for each individual and keeps records of their movement and maintains it.
Choosing the right type of access control system for your organization or home depends on various factors like the level of security you need, the number of users, the record you want to maintain and reports you want to generate. There isn’t any standard system which is considered the best fit for all. Hence, you need expert advice and support from the Access Control System service provider like us, Premware Services India LLP (Formally known as ‘PC Helpline’).
Access Control System Services we provide:
- Installation of Access Control System
- Maintenance of System
- Setting rules in RBAC
- Help in installing software to capture the records
Contact us today for your requirements of Access Control System in Surat, Gujarat.
FAQsFrequently Asked Questions and Answers on Access Control System
What are the 3 types of access control?
Below are the three types of access control systems:
- Discretionary Access Control (DAC)
- Mandatory Access Control (MAC)
- Role Based Access Control (RBAC)
How does access control system work?
Access Control Security System is an electronically configured box, wired internally with door to manage the locking and unlocking of the Gate, Door and Access Points. There are various techniques and protocols on which this box would operate. The system can be running on fingerprint or through RFID based door access control.
What are examples of an access control system?
Some examples of virtual and physical access control systems include:
- Login credentials (such as usernames and passwords).
- PINs and one-time passwords (OTPs).
- Virtual private network (VPN) access to internal networks.
- Physical access cards, FOBs, tokens, locks, and keys.
- Security guards with access lists.
- Biometric readers (such as for facial, retinal, and fingerprint scans).
- Digital authentication certificates and digital keys.
What is the goal of access control?
Access control is a fundamental component of data security that determines who is allowed to access and use company information and resources. Through authentication and authorization, access control policies ensure that users are who they say they are and that they have proper access to company data.
What is role based access control?
Role-Based Access Control (RBAC) is a method of restricting network access based on the roles of individual users within an enterprise. RBAC entitles employees to access only information that is necessary for them to perform their jobs and prevents them from accessing information that does not belong to them.
What are the three primary rules for RBAC?
According to Wikipedia, Three primary rules are defined for RBAC:
- Role assignment: A subject can exercise a permission only if the subject has selected or been assigned a role.
- Role authorization: A subject’s active role must be authorized for the subject. With rule 1 above, this rule ensures that users can take on only roles for which they are authorized.
- Permission authorization: A subject can exercise a permission only if the permission is authorized for the subject’s active role. With rules 1 and 2, this rule ensures that users can exercise only permissions for which they are authorized.
Give one example of role based access control?
Example of role based access control is a set of permissions that allow users to read, edit, or delete articles in a writing application.
What is Access control panels?
The Access Control Panel is the main backbone of the ACS with complete control of the entire system. The panel has various options which are configured as per the requirement and control/manage the locks based on the same.
